Ethical hacking involves attempts to hack through computer systems (with an owner’s permission) to find potential weaknesses and vulnerabilities, which hackers can exploit to access confidential data or valuable digital assets.
Once found, a security team can eliminate them to prevent exploitation threats. Hence, ethical hacking allows owners to control and minimize cybersecurity risks effectively.
Since cyber attacks have become more rampant and disastrous than ever, companies and enterprises across all industries need professional ethical hackers to test and strengthen their system security. Unsurprisingly, ethical hacking has become one of the most in-demand skills in the IT industry.
Because of this momentum, the skill becomes hugely lucrative as well. According to Glassdoor, an average ethical hacker in the US makes $114269 per month. Many elite specialists earn far more.
Furthermore, once you become an ethical hacker, you can earn additional income from bug bounty campaigns that companies worldwide give rewards to those who can find vulnerabilities in their systems. For example, in 2021 alone, Google paid as much as $8.7 million in rewards.
Hence, if you are interested in pursuing a career in Cybersecurity, ethical hacking is an excellent second or third course you want to take once you master the fundamentals.
This article will feature the best courses that will teach you general concepts and practical aspects of ethical hacking. You can then choose the right course that suits your preference and start learning right away.
Affiliate Disclosure: This post from Victory Tale contains affiliate links. We will receive a small commission from our partners if you purchase ethical hacking courses through them.
Nevertheless, we always value integrity and prioritize our audience’s interests. You can rest assured that we will present each course truthfully.
Things You Should Know
Scope of This Article
This article will only include courses that cover general concepts and practical applications of ethical hacking. It will not delve into CEH (Certified Ethical Hacker) training courses.
Prerequisites
Ethical hacking is not for absolute beginners. Before enrolling in any course, you should have foundational knowledge of the following:
- Networking (Ports, IP Address, etc.)
- Linux file structure and commands
- Windows Operating Systems
- Cybersecurity and cryptography (encryption and hashing)
- At least one programming language (Python, Java, C++, etc.), although Python is overwhelmingly preferred.
Note!
Some Udemy instructors may inform you that you don’t need to have the above knowledge because they will guide you through the basics in the course.
However, based on my observations, their training is rarely sufficient. Thus, you will be confused once you reach complex concepts. I, therefore, recommend taking courses on these topics before proceeding to ethical hacking training.
Criteria
Below are the criteria for the best ethical hacking courses:
- Taught by veteran cyber security experts with many years of relevant experience
- Available on a user-friendly learning platform
- Most of its course content must be up-to-date.
- Offer top-notch learning materials
- Provide excellent value for money
- Receive primarily positive reviews from actual students
- My personal experience with the instructor, course, and platform (if any) must be positive.
1. Ethical Hacker Nanodegree Program
This Nanodegree program by Udacity is unarguably one of the most comprehensive online programs on ethical hacking. You will learn from two leading experts who have been providing security solutions for numerous companies and government institutions.
Course Content
This program consists of two minor courses as follows:
1. Intro to Ethical Hacking – The first course will introduce you to crucial concepts, techniques, and procedures that ethical hackers must master. These include vulnerability management, system auditing, application auditing, social engineering, and open-source intelligence.
Upon completion, you will grasp all the tasks that you will be responsible for as an ethical hacker and be able to perform them effectively on your own.
2. Penetration Testing & Red Teaming Operations – The second course will drill deep into penetration testing. You will learn to perform all critical steps, from reconnaissance to gaining access and reporting what you have found.
Apart from the video lectures, there are quizzes and other assignments that you can complete to strengthen your ethical hacking knowledge.
Unlike most other ethical hacking courses, this one will provide you with hands-on experience through two real-world projects (one for each minor course.)
For example, you will perform a comprehensive security audit for a hypothetical IT company in the first course. You will be responsible for all the tasks and later write a report about your investigation.
These projects will thus simulate the tasks you will face as an ethical hacker, which is highly beneficial if you are determined to pursue this career path.
Udacity recommends spending 5-10 hours on the program, and you will complete it in two months. However, you should be prepared to spend longer hours than what Udacity suggests on the weekly assignments and projects since they can be highly challenging.
Student Support
Several ethical hacking courses do not provide sufficient student support. Thus, many students are left in the dark and have to spend hours figuring out complex stuff independently. However, this is not the case with Udacity.
Once you enroll in the Nanodegree program, Udacity will immediately offer you bootcamp-like assistance, including:
Technical Mentor Support – You can contact your mentor at any time (24/7) if you get stuck in coding assignments or encounter technical issues. This can be done easily by using the chat interface on Student Hub.
According to Udacity, most students receive personalized responses in less than an hour, which is super fast. You do not need to wait for weeks for an instructor’s response anymore.
Unlimited Project Reviews – As you work on two real-world projects, you can submit your work for an expert review at any time without the need to reach specific milestones. Experts will provide feedback along with tips, techniques, and best practices that you can implement to optimize your workflow.
Like technical mentor support, you should expect to receive feedback in no more than three hours. You can then submit several requests in a single day to ensure that your project is on the right track.
Career Services – The team will review your resume, LinkedIn profile, and Github portfolio to ensure that they properly showcase your newly acquired skills. This can help secure job interviews for highly competitive positions.
Pricing
The standard pricing for this Nanodegree program is $399 per month. However, you can opt for a 2-month bundle and receive a 15% discount, lowering tuition fees to $339 per month.
Furthermore, if you are a new student, you are eligible for personalized discounts. Just create an account and answer only two questions (like I did below). You will then gain access to a huge discount, which can be as high as 70% off.
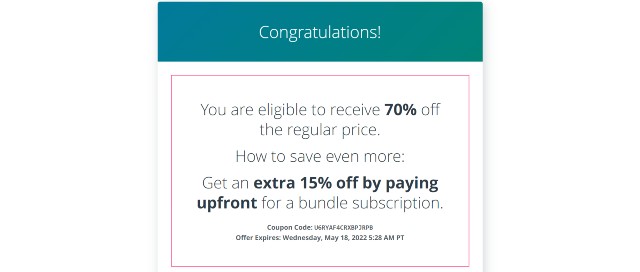
You can use this discount on top of the bundle. Therefore, it is possible to enroll in this top-notch program by investing only $100 per month.
[sc name=”udacity” ][/sc]Pros & Cons
Pros
- Undoubtedly one of the best online courses on ethical hacking
- Taught by experienced cybersecurity professionals with many years of experience in the field
- Comprehensive, up-to-date curriculum
- Self-paced learning
- Offer two real-world projects for students to complete to gain practical hands-on experience
- Provide timely, bootcamp-like student support
Cons
- Costlier than other alternatives
2. Learn Ethical Hacking From Scratch
This Udemy course is an excellent choice if you are looking for an introductory course to grasp the foundational concepts of ethical hacking. You will learn from Zaid Sabih, an ethical hacker and a pentester with more than a decade of professional experience.
Course Content
Below is a summary of all topics that you will learn in this 15.5-hour course:
- Introduction to Ethical Hacking + Kali Linux Installation
- Linux Basics
- Deep dive into network hacking: pre-connection attacks, gaining access (WEP/WPA/WPA2 Cracking), post-connection attacks (Information Gathering, MITM Attacks, Detection)
- Computer Device Hack: Server-side/Client-Side Attacks
- Post-exploitation
- Website Hacking (Information Gathering and Vulnerabilities Searching)
- and many more
The instructor’s teaching method is step-by-step. Each of his lessons is bite-sized, so it is easy to follow and beginner-friendly.
However, the curriculum is not comprehensive. You will need to take another online ethical hacking course if you want to delve into advanced concepts or procedures that a professional ethical hacker has to master.
Reviews: 4.6/5.0, Students: 495000+
Pros & Cons
Pros
- Taught by an experienced ethical hacker
- Beginner-friendly
- Well-structured curriculum
- Clear explanations of all concepts and ethical hacking processes
- 30-day money-back guarantee + Lifetime Access
- Inexpensive ($20 or lower when on sale)
Cons
- The curriculum is not comprehensive or in-depth. It barely touches intermediate/advanced concepts.
- Offer insufficient assignments and projects for students to complete
- Few sections are not up-to-date.
3. Learn Python & Ethical Hacking From Scratch
This course is again from Zaid Sabih. However, it features different content compared to the previous course. This one will teach you to create as many as 20+ Python programs from scratch to perform ethical hacking tasks.
Course Content
As a project-based course, you should prepare to get your hands dirty. The following is the list of Python programs that you will create in this 25-hour training:
- Media Access Control (MAC) Address Changer
- Network Scanner
- ARP Spoofer, Packet Sniffer, DNS Spoofer, File Interceptor, Code Injector, ARP Spoof Detector
- Malware (Keylogger, Backdoor, Packaging)
- Website Crawler
- Login Information Guessing Tool
- Vulnerability Scanner
The instructor will teach you how to build these tools from the beginning step-by-step. Regarding the theories and relevant techniques (such as bypassing HTTPS), he will allocate a few lessons to cover them.
However, you should not expect them to be as extensive as his other course. Because of this, I recommend taking both of his courses together.
The major drawback is that all content is based on Python 2. You will need to follow the instructions at the end of the course to port all programs to Python 3.
Reviews: 4.6/5.0, Students: 90000+
Pros & Cons
Pros
- Project-based learning: Students will learn to build as many as 20+ programs, earning substantial practical experience in the process.
- Bite-sized lessons with clear explanations
- Easy-to-follow curriculum
- 30-day money-back guarantee + Lifetime Access
- Inexpensive ($20 or lower when on sale)
Cons
- All lessons are in Python 2, which is outdated. You will need to follow the instructor’s guidance to port your programs to Python 3.
- The instructor does not give his students the solution code. However, he mentioned that this was intentional since he did not want them to copy and paste the solution code when they encountered issues. Still, this approach frustrated several students.
4. Complete Ethical Hacking Bootcamp 2023: Zero to Mastery
Suppose the second course is not informative enough. I suggest taking this one from Aleksa Tamburkovski, a freelance ethical hacker who works for enterprises and governments in identifying critical system vulnerabilities.
Note: You will use Python extensively to perform most of the tasks. However, informative Python training is already included in the course. You can take this course right away without taking another Python course.
Course Content
The following is what you will learn from this course:
- Introduction to Ethical Hacking + Installing Kali Linux Operating System
- Networking and Linux Review
- Reconnaissance and Information Gathering
- Scanning
- Vulnerability Analysis
- Exploitation & Gaining Access
- Viruses, Trojans, and Payloads
- Post-Exploitation
- Penetration Testing of web applications
- Man-in-the-middle attacks, Wireless Point Cracking, Hacking into Android devices, Methods to achieve anonymity
- and many more
This video content is 27.5 hours long. However, 9 hours of which are Python training. Hence, you will be left with 18.5 hours of ethical hacking content.
What I like about this course are its learning materials. All the slides are interactive, while all of their data are well-visualized. The instructor also adds multiple notes to clarify misunderstandings and complex stuff. Thus, students can grasp complicated concepts in no time.
Furthermore, there are three Python coding projects that you can complete to enhance your skills. Specifically, you will code a portscanner, create a backdoor, and build a bruteforcer. All of which are crucial skills that an ethical hacker must be proficient in.
Reviews: 4.7/5.0, Students: 43900+
Pros & Cons
Pros
- Taught by a veteran ethical hacker who is exceptionally knowledgable
- Comprehensive curriculum
- Informative lessons equipped with stunning, interactive visuals
- Provide additional notes and cheat sheets to help clarify complicated concepts
- Offer three coding projects for students to practice and gain hands-on experience
- 30-day money-back guarantee + Lifetime Access
- Inexpensive ($20 or lower when on sale)
Cons
- You will need to do your own research when completing projects. I think this is intentional as it simulates how an ethical hacker performs the tasks in real life. Still, such a process can be frustrating for some learners.
- Do not cover advanced concepts
- Some parts are a bit outdated.
5. The Complete Ethical Hacking Course
Are you looking for an all-in-one online course on ethical hacking? If so, I think this course by Atil Samancioglu is one you want to seriously consider.
Throughout the 38 hours of video content, Atil will guide you through the essence of ethical hacking and allow you to kickstart a compelling journey.
Course Content
What you will learn from this course is as follows:
- Python for Ethical Hacking – Data Types, Control Flows, Functions, Object-Oriented Programming (OOP)
- Introduction to Ethical Hacking + Virtual Machine and Kali Linux Installations
- Deep dive into Kali Linux
- How to obtain anonymity
- Introduction to the Dark Web
- Network Penetration Testing – Gathering Information, Wireless Attacks, Post-Connection Attacks
- System Hacking
- Attacks on Users
- Social Engineering & Social Media Security
- Beef & External Network Attacks
- Website Hacking – Reconnaissance, Cross Site Scripting (XSS), SQL Injection, etc.
- Website Penetration testing and relevant tools
- Building tools and learning other techniques – MAC Changer, Network Scanner, MITM, Packet Listener, Keylogger, Backdoor, Packaging Malicious Files
- and many more
This course extensively covers both theories and practicals in detail. Hence, it is optimal for those who want to learn ethical hacking but do not want to spend money on several training courses.
Reviews: 4.6/5.0, Students: 17900+
Pros & Cons
Pros
- Beginner-friendly
- Comprehensive, easy-to-follow curriculum
- Clear explanations of ethical hacking concepts and procedures
- 30-day money-back guarantee + Lifetime Access
- Inexpensive ($20 or lower when on sale)
Cons
- Some students believe the lessons are too basic, especially those in the first half of the course.
6. Applied Ethical Hacking and Rules of Engagement
Note
This course is no longer available in 2023!
This course by Seyed Farshid Miri delves into various complicated topics of ethical hacking, pen-testing, and threat hunting subjects. If you have taken other courses but believe that they are too shallow, you may want to try this one.
Course Content
The topics covered in this course are immense. Below is a summary of what you will learn from this 40-hour course:
- Set up your own hacking lab: Virtual Machine & Kali Linux Installations
- Introduction to Ethical Hacking
- Attack Vectors, Information Gathering, and Enumeration
- Vulnerability Scanning & Analysis
- Exploitation, Post-Exploitation, and Password Attacks
- Network Attacks
- Social Engineering Attacks
- Web App Penetration Testing (OWASP Top 10)
- Python Scripting
- Pentesting with CTFs (Capture The Flags)
- Deep dive into Red Teaming Operations
- Active Directory Attacks and MITRE ATT&CK Framework
- Introduction to Defensive Security
- Deep Dive into Elasticstack & Wazuh Manager (Setting up your SIEM, Integrating Endpoints, Index Life-Cycle Management, Threat Hunting, etc.)
This course is undoubtedly one of the most in-depth ethical hacking courses on Udemy. It covers both the theories and the applications extensively.
Based on my observations, many of its topics are rarely taught by other instructors. Therefore, if you are passionate about ethical hacking, I don’t think any other course will fit you more than this one.
Reviews: 4.7/5.0, Students: 75700+
Pros & Cons
Pros
- Taught by a knowledgeable instructor with more than 15 years of experience as a security specialist
- One of the few advanced courses to learn practical ethical hacking online, covering both offensive security (hacking techniques) and defensive mechanisms (Wazuh Manager)
- Informative lessons with real-life examples
- Well-structured curriculum
- Active Q&A forum
- 30-day money-back guarantee + Lifetime Access
- Inexpensive ($20 or lower when on sale)
Cons
- Several students believe the pace is too fast.
- Some parts of the course can be challenging for beginners.
Related Courses
SOC Analyst Training – This article covers the best courses that develop crucial skills for those who want to become SOC analysts.
Penetration Testing – Coming Soon
Network Security – Coming Soon
Enterprise Security – Coming Soon